Load Balancer¶
MedStack Control provides a pre-configured Traefik load balancer to accept connections from the internet and distribute traffic across the nodes in a cluster. A load balancer service is required in order to serve HTTPS services to the public internet.
👍 This service must be deployed
In order to make your applications available to the open internet and configure service ingress, you must deploy MedStack Control's load balancer service. If the load balancer is not deployed, it will not be possible to configure other services' domain mapping settings required for internal and external communication.
📘 Designed for load balancing and encryption only
There are many features of load balancers that are useful beyond enforcing encryption in transit. MedStack Control's managed load balancer service is not currently configurable for using other features such as authorization or sticky sessions.
Security¶
The load balancer oversees connections coming into the Docker environment from the internet. Traefik also handles the termination of HTTPS connections.
By default, all connections coming in from the internet are blocked and only connections that pass through the load balancer over ports 80 and 443 are allowed. Requests made to port 80 are automatically upgraded to port 443.
Cipher suites¶
When creating the load balancer service, it can be provisioned with the "most strict" or "most compatible" cipher suites used for certificate generation. We recommend the "most strict" cipher suites.
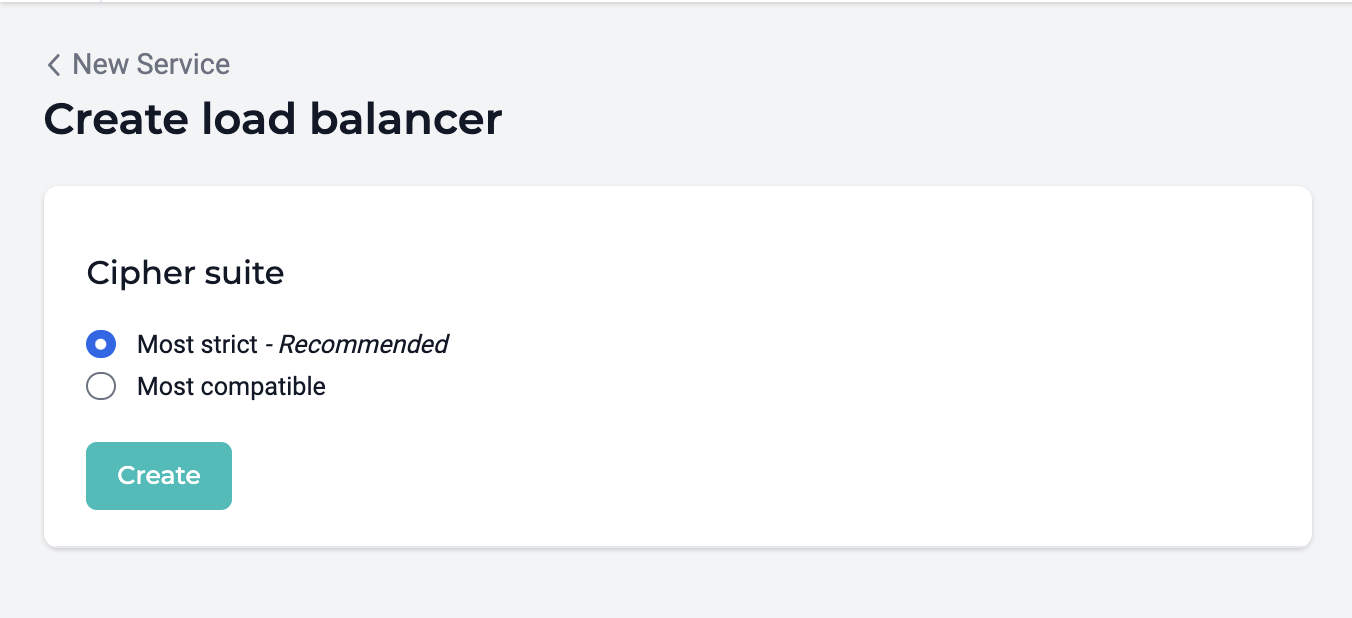
Most strict¶
This cipher suite contains ciphers listed in OWASP Category A. These are the strongest ciphers used for TLS encryption.
Most strict – OWASP Category A cipher suite
ciphers: {
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305,
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305"
}
Most compatible¶
This cipher suite contains ciphers listed in OWASP Category B. These are a broad collection of ciphers that will allow certificates to be generated for clients using less strict TLS encryption standards.
Most compatible – OWASP Category B cipher suite
ciphers: {
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305,
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,
TLS_RSA_WITH_AES_128_GCM_SHA256,
TLS_RSA_WITH_AES_256_GCM_SHA384,
TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA"
}
Certificates¶
Renewal¶
Traefik works with Let's Encrypt to automatically generate and renew certificates for the domains your Docker services depend on. As such, you do not need to manage the certificates for your domains accessible through services running on MedStack.
Certificates¶
The load balancer service creates a volume in the Docker environment labeled acme. If you need to access the certificates, you can mount the volume in a service, then access the certs in the application layer or by using the web terminal.
Connection protocol¶
Traefik secures your Docker environment by blocking all other incoming connections and proxies all incoming HTTPS connections through the service.
Any container will be proxied by the load balancer after adding ingress details in the service configuration form. The load balancer will automatically balance traffic across all of the containers that are connected to it.
Actions¶
Create¶
You can create the load balancer service and deploy instantly from the Docker configuration page in MedStack Control.
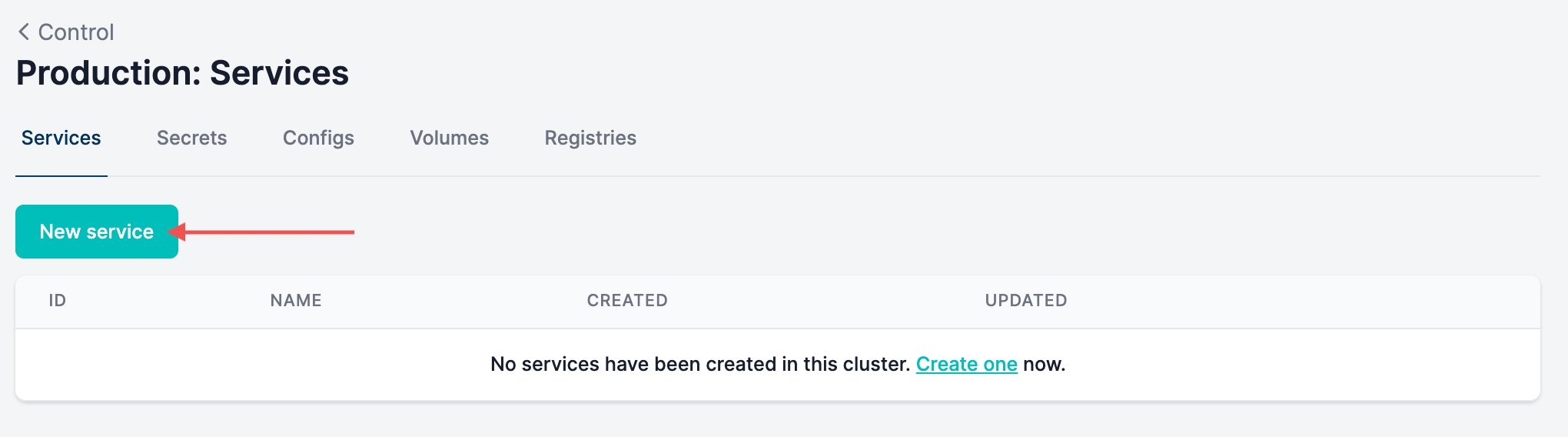
- Navigate to the Services tab and click the New service button.
- Select the Load Balancer service.
- Click the Create button.
The service will automatically deploy to the Docker environment. In the Volumes tab you will notice a volume called acme. This has been automatically created to store the SSL certificates.
Healthchecks¶
The load balancer supports healthchecks that determine if a container is unsuitable for receiving traffic. When a healthcheck fails, the load balancer will refrain from sending traffic to the container. The outcome of healthchecks can be viewed in the load balancer service logs.
Please note that load balancer healthchecks are different from Docker healthchecks.