Application requirements¶
In order to be able to deploy your applications to environments on MedStack Control, you'll need to ensure your applications:
- ✅ Have been containerized and capable of running in a Docker environment.
- ✅ Have container images stored in a private registry.
- ✅ Are built upon a Linux-based framework.
🚧 Not containerized yet?
To get started with containerization and running on Docker, we recommend reviewing Docker's quickstart guide.
Recommendations¶
Designing modular applications that hinge at the application layer make for the easiest migration to MedStack Control. We recommend you:
-
Build your applications using Docker Compose.
The MedStack Control interface is a translation of the way Docker Compose builds applications with inputs for services, configs, secrets, and volumes.
-
Design your applications to run in a way that is independent of orchestration technologies.
MedStack Control leverages Docker's orchestration layer, Docker Swarm, to run your containerized applications at scale. This layer is configured for privacy compliance by design. As such, Docker environment settings are not accessible. As a developer, you'll be able to SSH into containers, communicate over the Docker network, and perform actions within the capabilities of the containers.
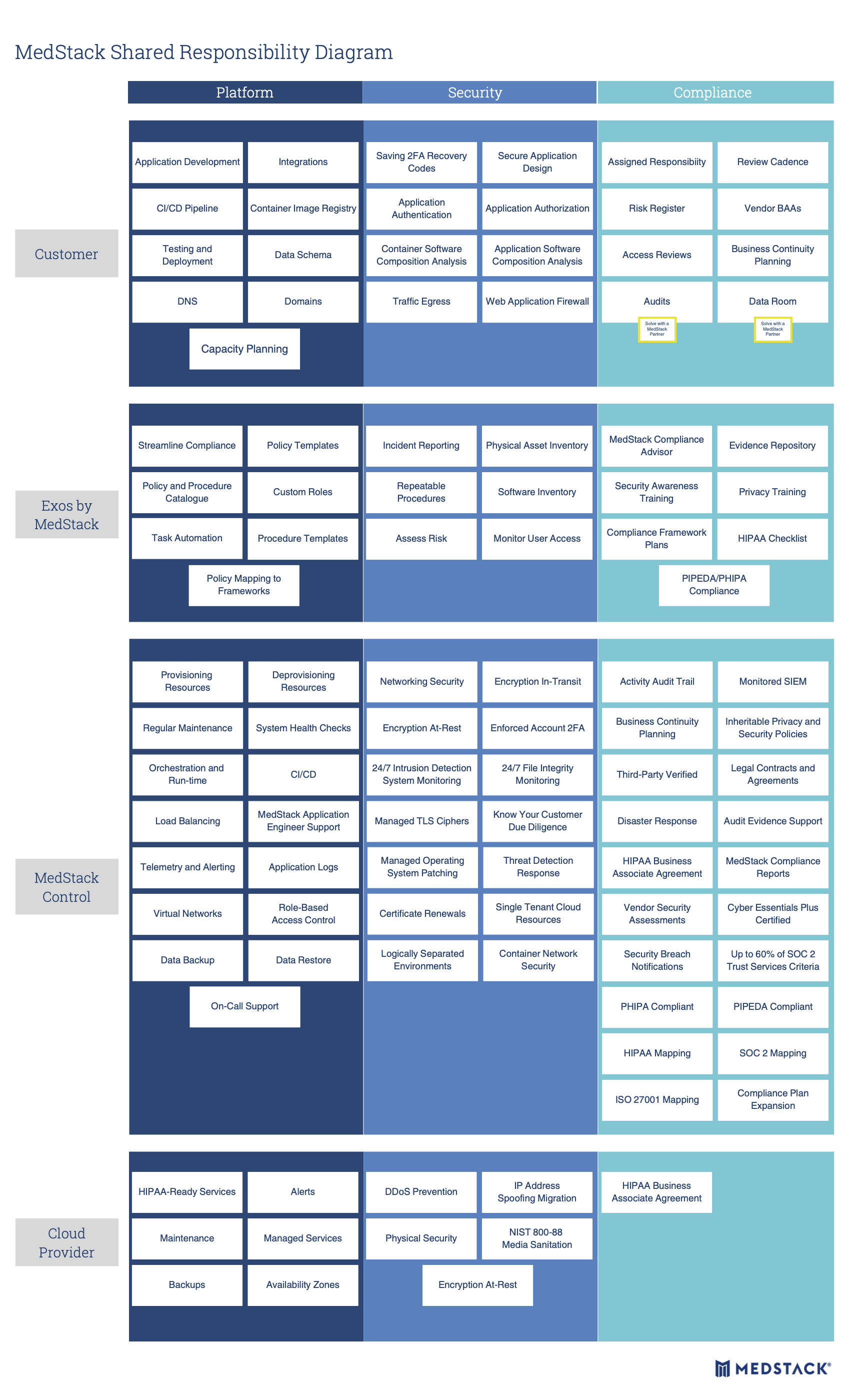
Shared responsibility diagram¶
It's important to understand the shared responsibility diagram when running your applications on MedStack Control. MedStack's products and services fit between the cloud provider's services and your application stack.
In MedStack Control, security sits at the core, defining aspects of the platform and compliance you inherit.